 A new Windows trojan has been discovered that attempts to steal passwords stored in the Google Chrome browser. While this is nothing unique, what stands out is that the malware uses a remote MongoDB database to store the stolen passwords.
A new Windows trojan has been discovered that attempts to steal passwords stored in the Google Chrome browser. While this is nothing unique, what stands out is that the malware uses a remote MongoDB database to store the stolen passwords.
This trojan is called CStealer, and like many other info-stealing trojans, was created to target and steal login credentials that were saved in Google Chrome’s password manager.
After being discovered by MalwareHunterTeam and further analyzed by James, though, things got a bit more interesting.
Instead of compiling the stolen passwords into a file and sending them to a C2 under the attackers control, the malware connects directly to a remote MongoDB database and uses it to store the stolen credentials.
To do this, the malware includes hardcoded MongoDB credentials and utilizes the MongoDB C Driver as a client library to connect to the database.
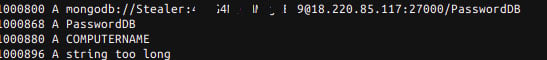
This is further illustrated by a test of the malware conducted by James. As you can see by the Wireshark screenshot below, when the malware steals Chrome passwords it will connect to the remote MongoDB database in order to store them for later retrieval by the attacker.
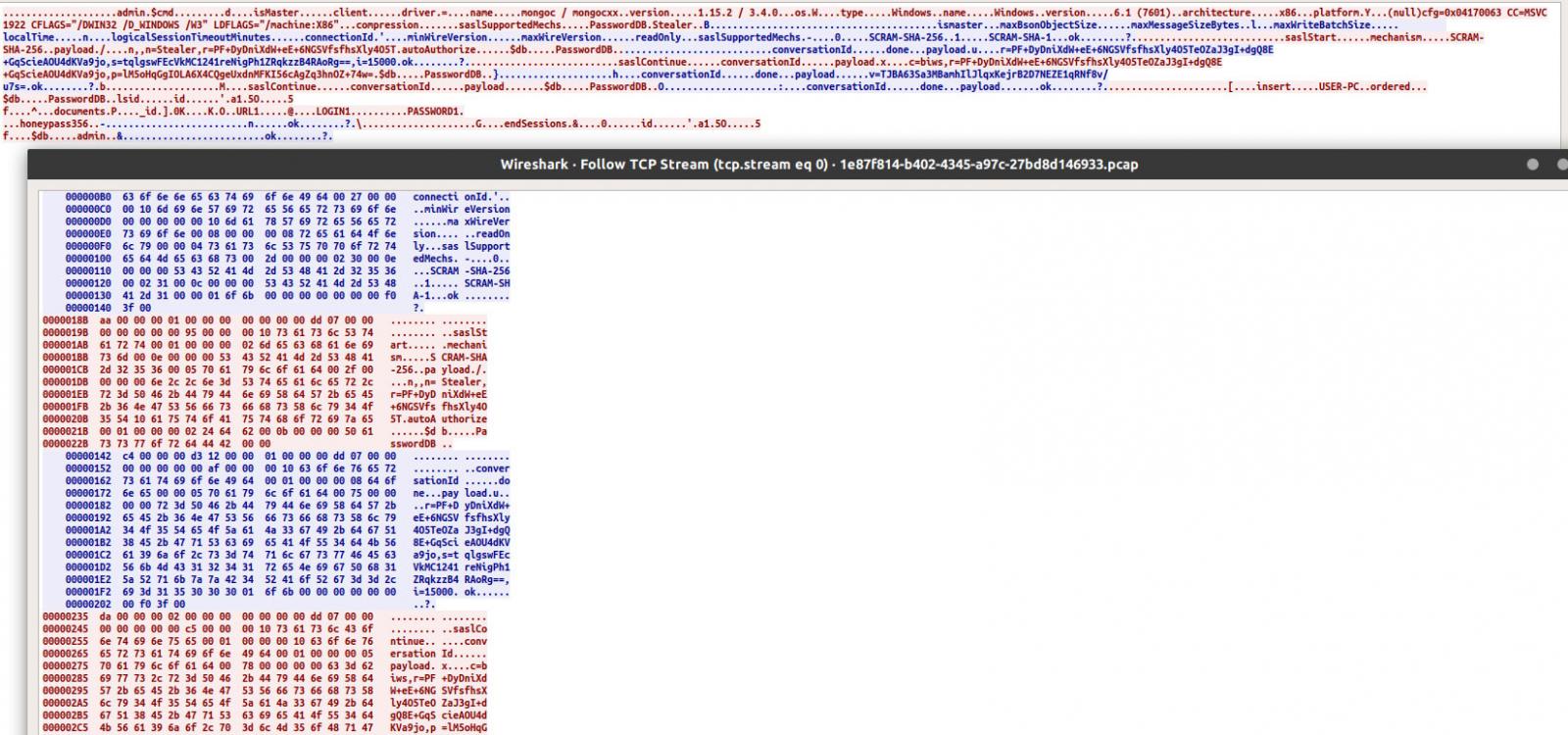
While this method ultimately serves its purpose of stealing passwords, it also opens the door for other attackers to gain access to the victim’s credentials.
All we can tell you is that you should always be aware of what you’re clicking. It’s easy to be fooled when we’re distracted. If you think you’re computer or network has been infultrated, scan your system with Malware Bytes or other reputable malware detection software to try to detect and remove it.













Leave A Comment
You must be logged in to post a comment.